Sideloadly has emerged as a popular tool for those looking to install apps outside the official app stores.
However, with its rise in popularity come concerns about safety and security.
This overview explores what Sideloadly is, the potential risks associated with its use, and the benefits it offers to both app developers and users.
A step-by-step guide on using Sideloadly safely and discussions on alternative installation methods are also included.
Whether you’re curious about sideloading or seeking safer options, this guide has you covered.
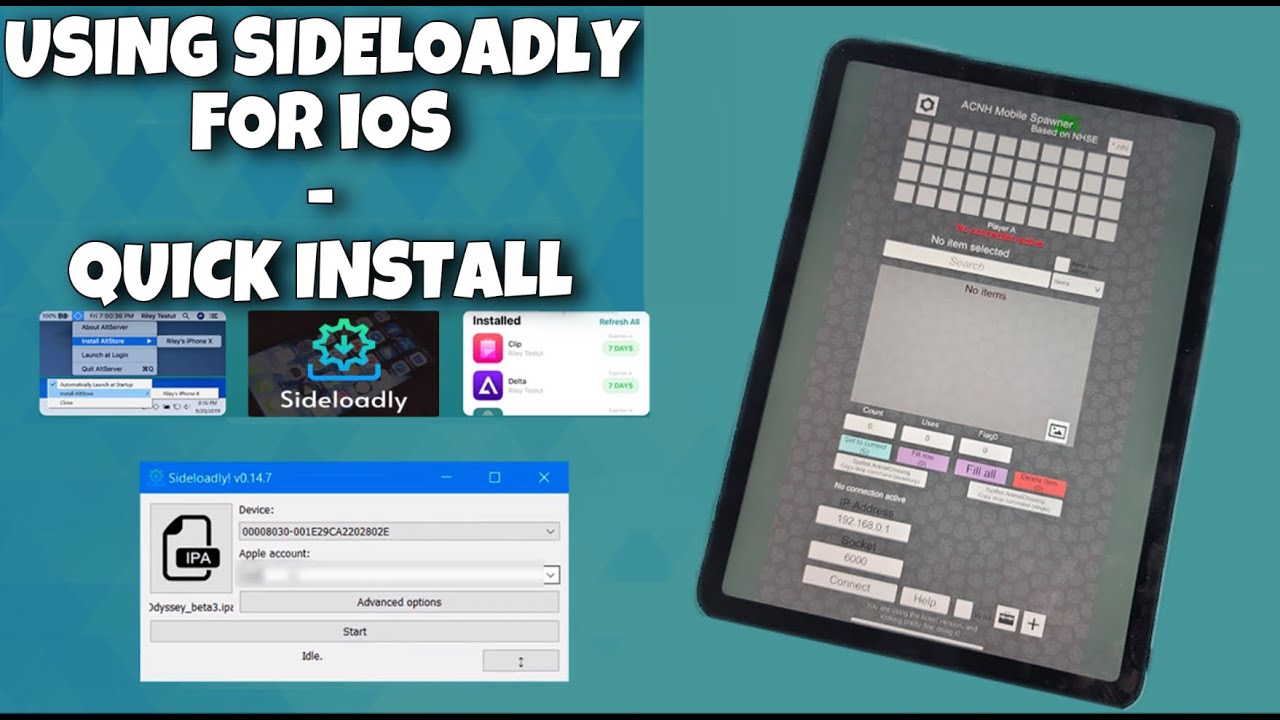
Sideloadly is a powerful tool designed for iOS users that allows the installation of third-party apps through sideloading, bypassing the limitations of the official App Store. This method enables users to install IPA files directly onto their iPhone, iPad, or iPod, offering a convenient way to access applications that may not be available through conventional channels.
Sideloading can be particularly beneficial for testing apps or using apps that require specific features not found in standard offerings. However, understanding the underlying processes, including device compatibility and application security, is crucial for a smooth experience.
Advantages for App Developers and Users
One of the primary advantages of using Sideloadly for both app developers and users is the streamlined process for app management and the ability to implement software updates efficiently.
This powerful tool not only simplifies the distribution of apps but also accelerates the testing phase, allowing developers to quickly gather user feedback and make necessary adjustments.
By eliminating cumbersome steps traditionally associated with app deployment, developers can focus on enhancing their creations and responding swiftly to user needs. As a result, the overall user experience improves significantly, with users enjoying timely access to new features and bug fixes.
This ease of app management fosters a positive relationship between developers and users, as well as encourages continuous engagement with applications.
How to Use Sideloadly Safely
To utilize Sideloadly safely, it’s essential to follow a structured installation process that includes thorough troubleshooting and obtaining proper user consent at each step.
Ensuring that the required permissions are granted and that security measures are in place will help protect against potential risks during the app installation phase.
By adhering to best practices, users can maximize their experience while minimizing exposure to unauthorized apps and malware, resulting in a secure and effective sideloading experience.
Step-by-Step Guide and Precautions
Following a step-by-step guide for using Sideloadly effectively involves a clear installation process, with precautions to ensure security and app verification throughout.
Users should begin by downloading the latest version of Sideloadly from a trusted source, as outdated or unofficial versions may pose security risks.
Once installed, connecting a compatible device is crucial; ensure to check for any required drivers. Ahead of installing any applications, it is advisable to conduct app verification to confirm their legitimacy.
Familiarizing oneself with troubleshooting steps, such as resolving potential connection issues and handling error messages, can further enhance the experience.
Implementing security measures, like using only official app sources and safeguarding personal information, will contribute to a safer installation process.
Comparing Different App Installation Methods
Comparing different app installation methods, including Sideloadly and others, helps users understand their options and choose the best fit for their needs.
Exploring these varied methods not only informs users about installation techniques but also enhances their overall experience with device management.
For instance, some users may find the standard installation from official app stores straightforward and hassle-free, while others might prefer Sideloadly for its ability to bypass certain restrictions.
Understanding troubleshooting steps relevant to each method can enable users to solve any issues that arise during installation.
By examining alternative methods, users can also discover unique solutions tailored to specific scenarios, thus ensuring they make informed decisions that best accommodate their preferences and requirements.